
Yakta Technologies provides industry-leading Information & Technology Solutions and ELV Security solutions. has a solid regional presence with operations in UAE.
We are a dedicated and loyal business in the Middle East to provide fully comprehensive Information & Technology Solutions and Services by professional engineers and world-class Technologies.
To accelerate our Client Transformations journey by delivering superior Services.
To get the customer's needs and provide products and appropriate solutions to fulfil their requirement.
To provide exceptional solutions and services to our Clients in a way that will offer concrete business benefits.
To be the region’s leading enterprise technology company, to get ready for future technology transformations.

IT infrastructure solutions in Dubai & Abu DhabiIT infrastructure in AbuDhabi, Dubai and the Middle East is gaining a growing reputation for taking on a more and more prominent role. This is because it enables companies to innovate and adapt quickly to changing business and technology environmen...

What is Data Center And Network Solution ?A data center network (DCN) connects a data center’s computing and storage units to achieve optimum performance. While some businesses still use on-premise data center networks and physical servers, many are moving to cloud-native environments.A data cente...

Firewall, UTM And VPN SolutionsA firewall is a critical network security device that plays a pivotal role in safeguarding your network from potential threats. By monitoring both incoming and outgoing network traffic, firewalls meticulously analyze data packets and determine whether to permit or deny...

How Voice over IP (VoIP) works is a mystery to some small business owners and employees. But if you understand how it works, you can more easily use the technology to your company's advantage.How VoIP Works: At a GlanceWith VoIP, analog voice calls are converted into packets of data. The packets tra...

As wiring and connection points evolved, more standardization was needed for cabling, connectors and the different types of wiring, including copper, fiber and coaxial. The American National Standards Institute and Telecommunications Industry Association set forth a series of standards, ANSI/TIA-568...

What is a point of sale (POS)?By definition, the point of sale (POS), or point of purchase, is the time and place in your retail store where transactions are completed. This is also known as the point of purchase. Think of the point of sale as your store’s checkout counter—the place where you ch...

Phone-based customer support remains one of the most popular support channels. It means that call centers are just as important as ever. As a result of this, there are so many solutions out there intended to help a call center function smoothly. There are different features available that will ...

Video and Audio ConferencingA Video and Audio Conferencing service is an Internet conferencing solution that combines both services into one integrated conferencing solution. Audio video conferencing service allows you to use traditional telephone access for the audio conference portion by dialing a...

A queue management system is a combination of tools both hardware and software and is being used to effectively manage and monitor the customer flow and to improve the customers’ experience and journey. As technology has advanced rapidly in the past few years so do the queue management systems too...

What is SMATV?SMATV stands for ‘Satellite Master Antenna Television’ and refers to a system that uses multiple satellite and broadcast signals to create a single integrated cable signal for distribution to a cabling network.How does it Work?SMATV systems generally work alongside an MATV system.&...

GRMS – GUEST ROOM MANAGEMENT SYSTEMThe main objective of using a GRMS – Guest Room Management System is to consistently satisfy guests’ needs and expectations in their rooms.The Guest Room Management System (GRMS) provides an innovative and efficient way to control the lighting, heating/coolin...

Closed-circuit television (CCTV), also known as video surveillance,[1][2] is the use of video cameras to transmit a signal to a specific place, on a limited set of monitors. It differs from broadcast television in that the signal is not openly transmitted, though it may employ point-to-point (P2P), ...

Geographical access control may be enforced by personnel (e.g. border guard, bouncer, ticket checker), or with a device such as a turnstile. There may be fences to avoid circumventing this access control. An alternative of access control in the strict sense (physically controlling access itself) is ...

An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations.[1] Any intrusion activity or violation is typically reported either to an administrator or collected centra...
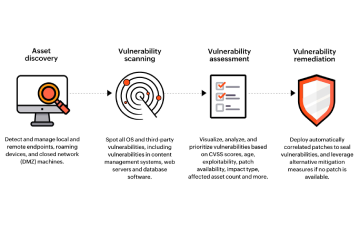
Before deploying a system, it first must go through from a series of vulnerability assessments that will ensure that the build system is secure from all the known security risks. When a new vulnerability is discovered, the system administrator can again perform an assessment, discover which modules ...

Car controls are the components in automobiles and other powered road vehicles, such as trucks and buses, used for driving and parking.While controls like steering wheels and pedals have existed since the invention of cars, other controls have developed and adapted to the demands of drivers. For exa...

A boom barrier, also known as a boom gate, is a bar, or pole pivoted to allow the boom to block vehicular or pedestrian access through a controlled point.[1] Typically, the tip of a boom gate rises in a vertical arc to a near vertical position. Boom gates are often counterweighted, so the pole is ea...

A public address system (or PA system) is an electronic system comprising microphones, amplifiers, loudspeakers, and related equipment. It increases the apparent volume (loudness) of a human voice, musical instrument, or other acoustic sound source or recorded sound or music. PA systems are used in ...

An intercom, also called an intercommunication device, intercommunicator, or interphone, is a stand-alone voice communications system for use within a building, small collection of buildings or portably within a small coverage area, which functions independently of the public telephone network.[1] I...

Smart Technologies (stylized as SMART Technologies)[2] also known as Smart, is a Canadian company headquartered in Calgary, Alberta, Canada and wholly owned by Foxconn.[2] Founded in 1987, Smart is best known as the developer of interactive whiteboards branded as the "SMART Board" popularly used in ...

Digital signage is a segment of electronic signage. Digital displays use technologies such as LCD, LED, projection and e-paper to display digital images, video, web pages, weather data, restaurant menus, or text. They can be found in public spaces, transportation systems, museums, stadiums, retail s...
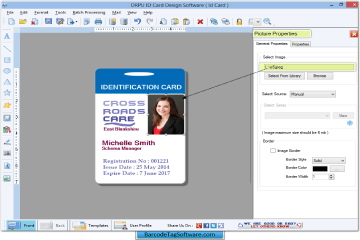
Express Excel ID card DesigningExpress Excel ID offers the core set of design tools many of which are typically found only in professional graphic design suites and unmatched by any other ID card software. Add text, logos, graphics, photos, and 1D barcodes to your badge design. Express ID is u...
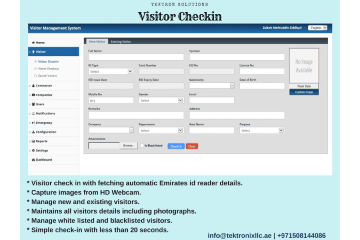
Visitor management refers to a set of practices or hardware additions that administrators can use to monitor the usage of a building or site. By gathering this information, a visitor management system can record the usage of facilities by specific visitors and provide documentation of visitor's wher...

Express ID Card Reader SoftwareThe Express ID is the Emirates ID Card Reader software used in a wide range of industries, such as: government and industry, security points, rental industry, education and financial institutions.Features of Express ID• Ability to read & save data, photographs &a...

Software asset management (SAM) is a business practice that involves managing and optimizing the purchase, deployment, maintenance, utilization, and disposal of software applications within an organization. According to ITIL, SAM is defined as “…all of the infrastructure and processes necessary ...
The first historically relevant year for the development of project management software is 1896, marked by the introduction of the Harmonogram. Polish economist Karol Adamiecki attempted to display task development in a floating chart, and laid the foundation for project management software as it is...

The point of sale (POS) or point of purchase (POP) is the time and place at which a retail transaction is completed. At the point of sale, the merchant calculates the amount owed by the customer, indicates that amount, may prepare an invoice for the customer (which may be a cash register printout), ...
Time-tracking software is a category of computer software that allows its employees to record time spent on tasks or projects. The software is used in many industries, including those who employ freelancers and hourly workers. It is also used by professionals who bill their customers by the hour. Th...

In computer security, general access control includes identification, authorization, authentication, access approval, and audit. A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authe...

An optical turnstile is a physical security device designed to restrict or control access to a building or secure area. Optical turnstiles are usually a part of an access control system, which also consists of software, card readers, and controllers. Optical turnstiles operate much like regular mech...

A revolving door typically consists of three or four doors that hang on a central shaft and rotate around a vertical axis within a cylindrical enclosure. Revolving doors are energy efficient as they, acting as an airlock, prevent drafts, thus decreasing the loss of heating or cooling for the buildin...
A security tour guard system is designed to help manage and monitor the activities of security personnel as they patrol a facility. Here’s a basic overview of how such systems typically work:Key Components1. Patrol Software: This is the central system that manages tour schedules, logs, and reports...